Documents, specifically records, do not spring into being for no purpose – they are created in support of business activities and Business Process Management solutions control business activities. Information Governance is all about keeping track – who, what, when, where, how – of business functions and the activities that support them. While managing records will always be important, it is also likely that the history of how that document/object flowed through an organization – its provenance – could be just as important.
There are a hundreds of benefits from using Business Process Management (BPM) / Workflow to facilitate Information Governance. Sarbanes Oxley triggered a slew of specialized workflow solutions for the purpose of managing financial data and approvals necessary for SOX reporting. But broader business process automation using Business Process Management / Workflow will bring significant Information Governance benefits to any organization.
When documents/records are created or added within a Business Process Management /Workflow instance they are, by default, properly categorized without any additional human interaction. Document categories (or types) are linked to the retention schedule allowing for automatic lifecycle control, especially when using an Enterprise Content Management solution. Critically, Business Process Management /Workflow keeps an audit trail of every action taken, every data element added or changed, approvals, all routings, etc. with date and time stamps all along the way.
Information Governance rules are effectively mandated and compliance audited with no additional effort when using Business Process Management / Workflow. Compare this approach to management-by-email: How often, in your own environment, does an overlooked email affect timelines of work? It’s just too easy for process flows to be broken with an ad hoc approach like email.
Too often, though, deploying Business Process Management /Workflow is considered complex, expensive and time consuming. It can be, with high volume, transactional processes like claims processing, but it doesn’t need to be nor should it be for typical compliance processes. Value will be realized faster if workflow can be deployed quickly. Jim Just’s Rule of Workflow Deployment is “Workflow deployment success is inversely proportional to deployment time.” In other words, deploy simply and quickly but have a program of continuous process improvement to enhance effectiveness and information governance over time.
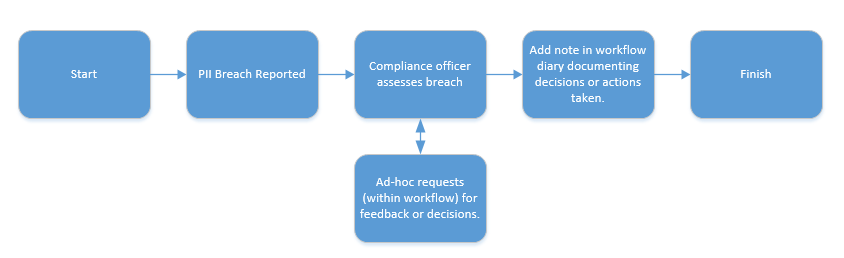
Even a simple and quick deployment yield significant benefits; let’s take the simplest of workflows using a PII breech as an example.
Even though there are no business rules, data lookups, or sophisticated routings, automating this process flow using Business Process Management /Workflow will gather in the audit trail:
- Incident report date and time
- Reporting individual
- Date and time compliance officer received the breech notice
- All individuals involved in review or approval (ad-hoc tasks)
- Breech resolution notes (workflow diary)
- Total time from breech incident open to closed
- Full reporting metrics proving compliance with policy and governance rules
Total time to setup and launch a simple workflow like this would be less than two days – less than one day with a mature workflow deployment team – and yet real, useful, defensible information will be gathered and held. Then, in the next iteration, more sophisticated rules, routings, eform for incident capture, etc. can be added by the Business Process Management /Workflow team.
If you aren’t using BPM to facilitate IG compliance, take the initiative to launch an automation program today – you’ll be glad you did.
If you want more discussion on how BPM can be used for Information Governance compliance, let me know and I’ll expand on this discussion in a later post. Or, contact me!
James Just, Partner
Phone: 608.239.8282
email: James.just@imergeconsulting.com
Twitter: @jamesJust10
LinkedIn: jamesjustimerge